Unraveling The Complexities Of Identity Fraud: A Deep Dive Into Identity Fraud Map 1
By admin / September 8, 2024 / No Comments / 2025
Unraveling the Complexities of Identity Fraud: A Deep Dive into Identity Fraud Map 1
Related Articles: Unraveling the Complexities of Identity Fraud: A Deep Dive into Identity Fraud Map 1
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unraveling the Complexities of Identity Fraud: A Deep Dive into Identity Fraud Map 1. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unraveling the Complexities of Identity Fraud: A Deep Dive into Identity Fraud Map 1
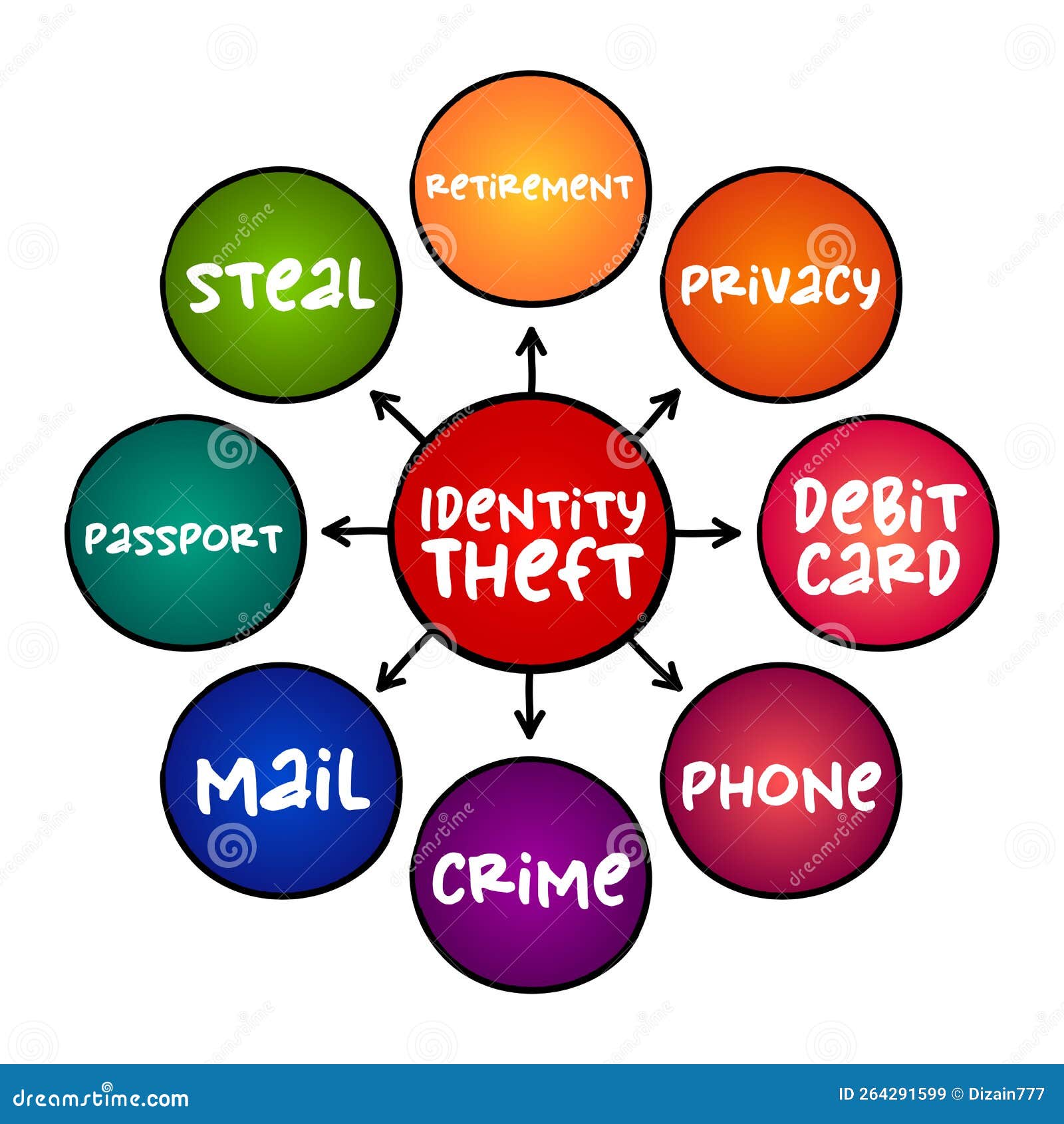
Identity theft, a pervasive and increasingly sophisticated crime, poses a significant threat to individuals and organizations alike. The intricate web of information that constitutes an individual’s identity, including personal details, financial records, and online presence, becomes a tempting target for malicious actors. To combat this growing menace, a comprehensive understanding of the various stages and tactics employed in identity fraud is crucial. This is where the Identity Fraud Map 1 emerges as a valuable tool, providing a structured framework to analyze and comprehend the multifaceted nature of identity theft.
Understanding the Landscape of Identity Fraud
Identity Fraud Map 1 is a conceptual model designed to illustrate the lifecycle of identity theft, from the initial stages of targeting and data collection to the ultimate exploitation of stolen information. It meticulously maps out the various stages of identity fraud, encompassing both traditional and digital methods, offering a comprehensive overview of the criminal landscape.
The Stages of Identity Fraud
The Identity Fraud Map 1 outlines four distinct stages in the lifecycle of identity theft:
1. Targeting: This stage involves the identification of potential victims and the gathering of information about them. Fraudsters often use data breaches, phishing campaigns, social engineering tactics, and public records to acquire personal details.
2. Data Collection: Once a target is identified, the next step involves collecting relevant information. This may include personal identification numbers (PINs), Social Security numbers (SSNs), credit card numbers, bank account details, and other sensitive data.
3. Account Takeover: In this stage, the stolen information is used to gain access to existing accounts or create new ones. Fraudsters may use the stolen data to open credit cards, apply for loans, or even access online accounts like email or social media platforms.
4. Exploitation: The final stage involves the exploitation of the compromised accounts for financial gain. Fraudsters may use stolen credit cards for unauthorized purchases, withdraw funds from bank accounts, or even sell the stolen data on the dark web.
The Importance of Identity Fraud Map 1
The Identity Fraud Map 1 serves as a valuable tool for various stakeholders, including law enforcement agencies, financial institutions, and individuals, by:
- Providing a framework for understanding the complexities of identity theft: The map helps to visualize the entire process, from the initial targeting to the final exploitation, enabling a comprehensive understanding of the criminal landscape.
- Identifying key vulnerabilities: By mapping the stages of identity theft, the model helps to identify potential weaknesses in security measures and identify areas for improvement.
- Facilitating collaboration and information sharing: The map provides a common language and understanding, fostering effective collaboration between law enforcement, financial institutions, and other stakeholders in combating identity fraud.
- Raising awareness among individuals and organizations: The map helps to educate individuals and organizations about the risks of identity theft and the importance of protecting personal information.
Frequently Asked Questions (FAQs) about Identity Fraud Map 1
Q: How can I use Identity Fraud Map 1 to protect myself from identity theft?
A: Understanding the stages of identity theft outlined in the map empowers individuals to take proactive measures to protect themselves. These include:
- Protecting personal information: Be cautious about sharing personal details online or over the phone.
- Monitoring credit reports: Regularly check your credit reports for any suspicious activity.
- Using strong passwords: Create strong and unique passwords for all online accounts.
- Being aware of phishing scams: Be wary of suspicious emails, phone calls, or text messages.
Q: What are the key takeaways from Identity Fraud Map 1 for businesses?
A: Businesses should implement robust security measures to protect their customers’ data. This includes:
- Data encryption: Encrypt sensitive data to prevent unauthorized access.
- Two-factor authentication: Implement two-factor authentication for all critical accounts.
- Employee training: Train employees about the risks of identity theft and best practices for data security.
Q: How can law enforcement agencies leverage Identity Fraud Map 1 to combat identity fraud?
A: Law enforcement agencies can use the map to:
- Develop targeted investigations: By understanding the stages of identity theft, law enforcement can prioritize investigations and focus on key areas of vulnerability.
- Improve data sharing and collaboration: The map provides a common framework for information sharing and collaboration between different agencies.
- Enhance prevention strategies: By understanding the tactics used by fraudsters, law enforcement can develop more effective prevention strategies.
Tips for Protecting Yourself from Identity Fraud
- Be cautious about sharing personal information online or over the phone. Avoid providing sensitive details to unknown sources or websites.
- Use strong and unique passwords for all online accounts. Avoid using the same password for multiple accounts.
- Monitor your credit reports regularly. Check for any suspicious activity and report any errors immediately.
- Be aware of phishing scams. Be wary of suspicious emails, phone calls, or text messages that ask for personal information.
- Shred sensitive documents before discarding them. This prevents criminals from accessing your personal information from trash.
- Consider using a credit monitoring service. These services can alert you to any suspicious activity on your credit reports.
Conclusion
The Identity Fraud Map 1 provides a powerful tool for understanding and combating the growing threat of identity theft. By outlining the stages of identity fraud, the map helps to identify vulnerabilities, facilitate collaboration, and empower individuals and organizations to take proactive measures to protect themselves. Through a combined effort of education, awareness, and robust security measures, we can effectively mitigate the risks of identity theft and protect our personal and financial information.


.png/revision/latest?cb=20190702211210)
Closure
Thus, we hope this article has provided valuable insights into Unraveling the Complexities of Identity Fraud: A Deep Dive into Identity Fraud Map 1. We thank you for taking the time to read this article. See you in our next article!